Overview:
Function selectors are a way of identifying functions in EVM (Ethereum Virtual Machine) smart contracts. These function signatures are hashed using the keccak256 algorithm, and the first 4 bytes of the resulting hash are used as the function selector. This allows for the identification of the function and the parameters it takes, so that the caller can provide the correct information and the correct function can be called by the smart contract.
In this post I will go over how it is posible to change the function selectors of smart-contracts after they have been compiled to bytecode. I will also go over some of the reasons someone might want to do this, or how it could potentially be used in real situations.
What is a Function Selector
Function selectors are the first four bytes of the Keccak-256 (SHA-3) hash of a function’s signature. A function signature is made up of the function’s name and the types of its arguments. In Ethereum, the Keccak-256 hash of a function signature is used to identify which function is being called when a contract receives a message. This allows multiple functions with the same name but different argument types to exist within a contract and be distinguished from one another.
For example, the function signature transfer(address sender, uint256 amount) would be hashed with Keccak-256 to produce a function selector of 0xa9059cbb. Similarly, the function signature withdraw(uint256 wad) would be hashed to produce a function selector of 0x2e1a7d4d.
Function selectors are important because they allow the caller of a contract to specify the exact function they want to call, along with the necessary arguments. This ensures that the correct function is called and that the contract has the necessary information to execute it.
You can find more information and examples of function selectors on the Solidity By Example website, which has a section dedicated to this topic: Here.
My Usecase
I recently learned that it’s possible to modify function selectors in order to make it difficult to detect the use of unknown smart contracts. This can be useful for mitigating the risk of using unknown code, but it’s important to note that this approach is not practical or safe as it relies on flying blind without access to the source code. However, for those who are interested in learning more about this technique and my personal use case, here’s how it works:
First, it’s important to understand that all bytecode is available on the blockchain network. This means that it’s possible to use already deployed smart contract bytecode for your own purposes, although this comes with its own set of risks. In order to make it less obvious that you’re using unknown code, you can create another smart contract that calls your first contract, changing the function hashes used. This makes it difficult to detect with tools like etherscan.
However, there’s a catch: smart contract addresses are not the same as normal user signing addresses, so any functions that use require _param1 == addr(_param1) will revert instantly. This means that you need to find a different way to modify the function selectors.
One approach is to use the fact that hashed functions don’t care about their original names or parameters. Because hashes are a one-way operation, you can change them to anything you want and call them with the new function hash. This will work for some hex codes but not others, and the reason for this is that the compiler does a small optimization for function calls. By using a decompiler like ethervm.io, you can see that for most smart contracts the compiler finds the function hash that is numerically between the others and uses it to search for the matching function selector above and below it. This cuts the search time roughly in half.
Once you understand this, you can change your function hashes, deploy your smart contracts, and hopefully be undetected. However, it’s important to keep in mind that this approach is not practical or safe, and is only recommended as a learning experience. As you gain more knowledge and experience in smart contract design and efficiency, you can move on to creating your own robust smart contracts.
Identifying Function Selectors
First, you will need the bytecode of your target contract that was used in the smart contract creation. There are two types of bytecode, usually named “bytecode” and “deployed bytecode.” If you are not familiar with the difference between the two, you can read about it in this Medium post: The difference between bytecode and deployed bytecode.
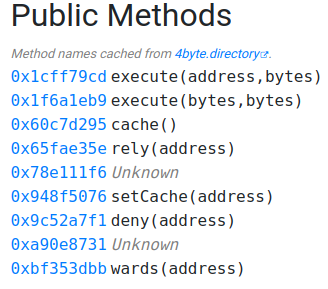
To obtain the function hashes, you can use a tool like ethervm.io. For this example, we will be using a unknown MEV Bot smart contract on the Ethereum network. Take the deployed bytecode from etherscan and paste it into the text box at the bottom of ethervm.io. Alternatively, you can use the contract address and hit “decompile.” This will give you a decompiled version of the contract, which you can view here.
Once you have the decompiled contract, you can identify the functions in the hex-compiled smart contract code, also known as the bytecode. In this example, we will change the 0x1cff79cd execute(address,bytes), 0x78e111f6 Unknown, and 0x9c52a7f1 deny(address) functions.
Note: Using the ethervm.io decompiler requires “deployed bytecode” as input but for the rest of this post we will be working with “bytecode”.
Note: “Bytecode” can be found in the Input Data field of the transaction that created the smart contract. For example the MEV bot’s creation transaction Here
Full Bytecode
1
0x608060405234801561001057600080fd5b50604051602080610d628339810180604052602081101561003057600080fd5b5051336000908152602081905260409020600190556100578164010000000061005e810204565b5050610114565b3360009081526020819052604081205460011461007a57600080fd5b600160a060020a03821615156100f157604080517f08c379a000000000000000000000000000000000000000000000000000000000815260206004820152601f60248201527f64732d70726f78792d63616368652d616464726573732d726571756972656400604482015290519081900360640190fd5b5060018054600160a060020a038316600160a060020a0319909116178155919050565b610c3f806101236000396000f3fe6080604052600436106100a3576000357c01000000000000000000000000000000000000000000000000000000009004806378e111f61161007657806378e111f6146102ec578063948f5076146104175780639c52a7f11461045e578063a90e873114610491578063bf353dbb146105be576100a3565b80631cff79cd146100a55780631f6a1eb91461015b57806360c7d2951461028857806365fae35e146102b9575b005b6100a3600480360360408110156100bb57600080fd5b600160a060020a0382351691908101906040810160208201356401000000008111156100e657600080fd5b8201836020820111156100f857600080fd5b8035906020019184600183028401116401000000008311171561011a57600080fd5b91908080601f016020809104026020016040519081016040528093929190818152602001838380828437600092019190915250929550610603945050505050565b6100a36004803603604081101561017157600080fd5b81019060208101813564010000000081111561018c57600080fd5b82018360208201111561019e57600080fd5b803590602001918460018302840111640100000000831117156101c057600080fd5b91908080601f016020809104026020016040519081016040528093929190818152602001838380828437600092019190915250929594936020810193503591505064010000000081111561021357600080fd5b82018360208201111561022557600080fd5b8035906020019184600183028401116401000000008311171561024757600080fd5b91908080601f016020809104026020016040519081016040528093929190818152602001838380828437600092019190915250929550610645945050505050565b34801561029457600080fd5b5061029d610847565b60408051600160a060020a039092168252519081900360200190f35b3480156102c557600080fd5b506100a3600480360360208110156102dc57600080fd5b5035600160a060020a0316610856565b6103a26004803603604081101561030257600080fd5b600160a060020a03823516919081019060408101602082013564010000000081111561032d57600080fd5b82018360208201111561033f57600080fd5b8035906020019184600183028401116401000000008311171561036157600080fd5b91908080601f01602080910402602001604051908101604052809392919081815260200183838082843760009201919091525092955061088f945050505050565b6040805160208082528351818301528351919283929083019185019080838360005b838110156103dc5781810151838201526020016103c4565b50505050905090810190601f1680156104095780820380516001836020036101000a031916815260200191505b509250505060405180910390f35b34801561042357600080fd5b5061044a6004803603602081101561043a57600080fd5b5035600160a060020a03166108fa565b604080519115158252519081900360200190f35b34801561046a57600080fd5b506100a36004803603602081101561048157600080fd5b5035600160a060020a03166109bd565b6103a2600480360360408110156104a757600080fd5b8101906020810181356401000000008111156104c257600080fd5b8201836020820111156104d457600080fd5b803590602001918460018302840111640100000000831117156104f657600080fd5b91908080601f016020809104026020016040519081016040528093929190818152602001838380828437600092019190915250929594936020810193503591505064010000000081111561054957600080fd5b82018360208201111561055b57600080fd5b8035906020019184600183028401116401000000008311171561057d57600080fd5b91908080601f0160208091040260200160405190810160405280939291908181526020018383808284376000920191909152509295506109f3945050505050565b3480156105ca57600080fd5b506105f1600480360360208110156105e157600080fd5b5035600160a060020a0316610c01565b60408051918252519081900360200190f35b3360009081526020819052604090205460011461061f57600080fd5b600080825160208401855af480156001811461063a5761063f565b600080fd5b50505050565b6001546040517f8bf4515c000000000000000000000000000000000000000000000000000000008152602060048201818152855160248401528551600094600160a060020a031693638bf4515c938893928392604401918501908083838b5b838110156106bc5781810151838201526020016106a4565b50505050905090810190601f1680156106e95780820380516001836020036101000a031916815260200191505b509250505060206040518083038186803b15801561070657600080fd5b505afa15801561071a573d6000803e3d6000fd5b505050506040513d602081101561073057600080fd5b50519050600160a060020a0381161515610838576001546040517f7ed0c3b2000000000000000000000000000000000000000000000000000000008152602060048201818152865160248401528651600160a060020a0390941693637ed0c3b293889383926044909201919085019080838360005b838110156107bd5781810151838201526020016107a5565b50505050905090810190601f1680156107ea5780820380516001836020036101000a031916815260200191505b5092505050602060405180830381600087803b15801561080957600080fd5b505af115801561081d573d6000803e3d6000fd5b505050506040513d602081101561083357600080fd5b505190505b6108428183610603565b505050565b600154600160a060020a031681565b3360009081526020819052604090205460011461087257600080fd5b600160a060020a0316600090815260208190526040902060019055565b336000908152602081905260409020546060906001146108ae57600080fd5b600080835160208501865af43d6040519250601f19601f6020830101168301604052808352806000602085013e8115600181146108ea576108f1565b8160208501fd5b50505092915050565b3360009081526020819052604081205460011461091657600080fd5b600160a060020a038216151561098d57604080517f08c379a000000000000000000000000000000000000000000000000000000000815260206004820152601f60248201527f64732d70726f78792d63616368652d616464726573732d726571756972656400604482015290519081900360640190fd5b5060018054600160a060020a03831673ffffffffffffffffffffffffffffffffffffffff19909116178155919050565b336000908152602081905260409020546001146109d957600080fd5b600160a060020a0316600090815260208190526040812055565b6001546040517f8bf4515c000000000000000000000000000000000000000000000000000000008152602060048201818152855160248401528551606094600094600160a060020a0390911693638bf4515c93899390928392604490910191908501908083838b5b83811015610a73578181015183820152602001610a5b565b50505050905090810190601f168015610aa05780820380516001836020036101000a031916815260200191505b509250505060206040518083038186803b158015610abd57600080fd5b505afa158015610ad1573d6000803e3d6000fd5b505050506040513d6020811015610ae757600080fd5b50519050600160a060020a0381161515610bef576001546040517f7ed0c3b2000000000000000000000000000000000000000000000000000000008152602060048201818152875160248401528751600160a060020a0390941693637ed0c3b293899383926044909201919085019080838360005b83811015610b74578181015183820152602001610b5c565b50505050905090810190601f168015610ba15780820380516001836020036101000a031916815260200191505b5092505050602060405180830381600087803b158015610bc057600080fd5b505af1158015610bd4573d6000803e3d6000fd5b505050506040513d6020811015610bea57600080fd5b505190505b610bf9818461088f565b949350505050565b6000602081905290815260409020548156fea165627a7a72305820d2cb37091b9fea78618babf87ea1e2213f2acdaa5676752f200e6d4bdd52ab080029000000000000000000000000f3c9d00c06e6ceef470510ed599bd30569a2ddc6
Shortened Bytecode With Functions Highlighted 0x608060405234801561001057600080fd5b50604051602080610d628339810180604052602081101561003057600080fd5b5051336000908152602081905260409020600190556100578164010000000061005e810204565b5050610114565b3360009081526020819052604081205460011461007a57600080fd5b600160a060020a03821615156100f157604080517f08c379a000000000000000000000000000000000000000000000000000000000815260206004820152601f60248201527f64732d70726f78792d63616368652d616464726573732d726571756972656400604482015290519081900360640190fd5b5060018054600160a060020a038316600160a060020a0319909116178155919050565b610c3f806101236000396000f3fe6080604052600436106100a3576000357c01000000000000000000000000000000000000000000000000000000009004806378e111f61161007657806378e111f6146102ec578063948f5076146104175780639c52a7f11461045e578063a90e873114610491578063bf353dbb146105be576100a3565b80631cff79cd146100a55780631f6a1eb91461015b57806360c7d2951461028857806365fae35e146102b9575b005b6100a3600480360360408110156100bb57600080fd5b600160a060020a0382351691908101906040810160208201356401000000008111156100e657600080fd5b8201836020820111156100f857600080fd5b8035906020019184600183028401116401000000008311171561011a57600080fd5b919080806…
Note: 78e111f6 gets used twice in the bytecode we will change both.
Changing Function Selectors
We can change the 4-byte function selectors in our bytecode to any desired value, with one notable exception. Depending on how the bytecode is compiled, the compiler may optimize it in order to improve the speed at which functions are called. If the bytecode you are modifying has a small number of functions, you may be able to ignore this optimization. However, this is often not the case.
For example, the Weth9 contract uses a if (var0 == "function selector" operation to find the correct function selector, while our example Mev Bot contract uses an if (0x78e111f6 > var0) statement first then a if (var0 == "function selector" to find the function selector. This is because the Mev Bot contract was optimized to use less gas when looking up functions.
Because of this optimization, we must take it into account when modifying our bytecode.
Note: Complicated and heavily optimized contracts may have nested if statements adding to complexity.
In our example, we need to pick a new function that is either smaller or larger than the numerical midpoint function, depending on whether the original function was smaller or larger than the midpoint function. For instance, if the midpoint function is 0x78e111f6 and we want to replace 0x1cff79cd, we need to choose a hex number that is smaller than 0x78e111f6. If we want to replace 0x9c52a7f1, we need to choose a hex number that is larger than 0x78e111f6. However, we can also change the midpoint function itself. Keep in mind, though, that because the bytecode has already been compiled, changing the midpoint function will not change the order of the functions or which functions are greater than or less than the midpoint function. For example, if we change the midpoint function to the largest possible hex number 0xffffffff, we can choose any new hash function for 0x1cff79cd, but we won’t be able to use any hex number for 0x9c52a7f1, because there is no function that is greater than 0xffffffff. Similarly, if we set the midpoint function to 0x00000000, only functions that were originally bigger than the original midpoint would be changeable. It’s also worth noting that changing two or more hashes to the same hash can create unique scenarios that may not be desirable.
Now that we have changed one or all of the function hashes in our smart contract, we can deploy it using a tool that allows us to send a transaction with the data field. Some popular options include ethersJS with hardhat or 0xPhaze’s ABI Playground. Once the transaction is mined, you can use your contract with the updated function hashes.
You can call the functions in your contract by creating your own transaction data, or by using a devloper-friendly tool such as hardhat. Keep in mind that the functions will still perform the same tasks as before, but will now have different function selectors.
Overall, changing the function hashes in a smart contract allows you to deploy an updated version of the contract, while still retaining its original functionality.
Real-World Implications
The main reason for changing a function selector in bytecode which I detailed in the My Usecase section is to obfuscate the functions and their purposes. This can help prevent others from easily identifying and interacting with your contract, and make it harder for them to attack it. For example, there are databases like the 4byte database that contain hashes of well-known functions from verified code and GitHub projects, which makes it easier for people to see what functions a contract uses and interact with them without having the source code. By changing the function selectors, you can make it more difficult for others to detect and access your contract while still using the same bytecode.
Note: An easier way to change function selectors if you have the source code is to change the function names before compilation.
One potential consequence of this knowledge is the potential for malicious use. Because we can change the function hash to any value we want, it is possible to change it to a common function found in databases. This could be a problem if you trust a contract solely based on the function name appearing in a service like Etherscan, MetaMask, or any other wallet provider. Etherscan will only look at the function hash in the transaction data field and assign the function name without verifying the contract. Additionally, this vulnerability can be exploited by creating a function with the same name and parameters in the contract’s source code. Anyone aware of this possibility should be able to avoid falling victim to this trick, but it is important to keep this potential vulnerability in mind for those who use and trust these tools.
Conclusion
I hope you enjoyed this novel approach to modifying post-compiled EVM bytecode function selectors. I couldn’t find any other information on this topic online, so I decided to share what I’ve learned. If anyone else has discovered this, or if you have any questions or feedback, feel free to reach out to me. Thanks for reading!
P.S. I recommend giving this a try out yourself with tools such as ethersJS with hardhat or 0xPhaze’s ABI Playground and see what you can do.
